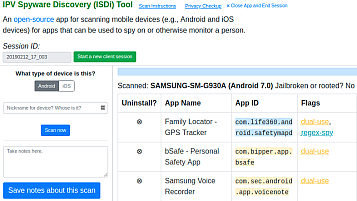
Checks Android or iOS devices for apps used to surveil or track victims ("stalkerware", "spouseware", "spyware"). ISDi's technical details are included in "Clinical Computer Security for Victims of Intimate Partner Violence" (USENIX 2019). The blacklist is based on apps crawled in "The Spyware Used in Intimate Partner Violence" (IEEE S&P 2018).
Contribution Guidelines
For more information about contributing to ISDi, see the contribution guidelines.
Installing ISDi 
Right now, ISDi currently only natively supports macOS and Linux. If you are using a Windows device, you can use the Windows Subsystem for Linux 2 (WSL2), which can be installed by following these instructions. After this, follow the remaining instructions as a Linux user would, cloning/running ISDi inside the Linux container of your choice.
--------
Presentation in "28th USENIX Security Sympoosium"
Clinical Computer Security for Victims of Intimate Partner Violence
Sam Havron, Diana Freed, and Rahul Chatterjee, Cornell Tech; Damon McCoy, New York University; Nicola Dell and Thomas Ristenpart, Cornell Tech
Digital insecurity in the face of targeted, persistent attacks increasingly leaves victims in debilitating or even life-threatening situations. We propose an approach to helping victims, what we call clinical computer security, and explore it in the context of intimate partner violence (IPV). IPV is widespread and abusers exploit technology to track, harass, intimidate, and otherwise harm their victims. We report on the iterative design, refinement, and deployment of a consultation service that we created to help IPV victims obtain in-person security help from a trained technologist. To do so we created and tested a range of new technical and non-technical tools that systematize the discovery and investigation of the complicated, multimodal digital attacks seen in IPV. An initial field study with 44 IPV survivors showed how our procedures and tools help victims discover account compromise, exploitable misconfigurations, and potential spyware.
USENIX Security '19 Open Access Videos Sponsored by
King Abdullah University of Science and Technology (KAUST)
Open Access Media
USENIX is committed to Open Access to the research presented at our events. Papers and proceedings are freely available to everyone once the event begins. Any video, audio, and/or slides that are posted after the event are also free and open to everyone. Support USENIX and our commitment to Open Access.
author = {Sam Havron and Diana Freed and Rahul Chatterjee and Damon McCoy and Nicola Dell and Thomas Ristenpart},
title = {Clinical Computer Security for Victims of Intimate Partner Violence},
booktitle = {28th USENIX Security Symposium (USENIX Security 19)},
year = {2019},
isbn = {978-1-939133-06-9},
address = {Santa Clara, CA},
pages = {105--122},
url = {https://www.usenix.org/conference/usenixsecurity19/presentation/havron},
publisher = {USENIX Association},
month = aug,
}
Materials and protocols on CETA (Clinic to End Tech Abuse)
Resources |
This page provides a collection of materials, tools, and resources that we have created to help IPV survivors, support workers, and technologists discover and address tech-related risks.
All of our resources are free to download and use. We use many of them as part of our Computer Security Clinic for IPV survivors in New York City.
Our step-by-step how-to guides can be especially useful for providing help remotely.
Compiled by CETA Volunteers
- Disconnecting from your ex-partner - a checklist (short version)
- Disconnecting from your ex-partner - a checklist (long version)
- Checking your smartphone or tablet for spyware
- Gmail and Google apps - turning on extra security
- Gmail - checking for suspicious logins
- Gmail and Google - cleaning up privacy and security problems
- Google Chrome - privacy checkup
- Android phones - checking for hidden apps and side-loaded apps (from an unofficial app store)
- iCloud -- cleaning up privacy and security problems
- iCloud - turning on extra security
- iCloud - checking for suspicious logins using a Mac laptop
- Facebook - turning on extra security
- Facebook - cleaning up privacy and security problems
- Instagram - cleaning up privacy and security problems
- WhatsApp - security tips
- TikTok - Checking for Account Compromise and Increasing Security
- Hotmail - Checking Privacy and Security Settings
- Yahoo - checking for suspicious logins
- Password managers
Other Clinic Resources
Compiled by CETA Volunteers
- Tech Clinic Consultation Protocol
- Technology Assessment Questionnaire
- Technograph
- App Classification Guide
- IPV Spyware Discovery Tool (ISDi)
Related news:
- A bill aims to stop abusers stalking ex-partners. US telecom firms are lobbying against it
- Domestic Abusers Can Control Your Devices. Here’s How to Fight Back